A recipe for setting up permissions to run ExMerge
I have seen a number of questions relating to getting ExMerge running in Exchange 2000/2003. The quickest and dirtiest way to do this is to clear the Send As and Receive As "explicit denies" on the Exchange organization object for Domain Admins and Enterprise Admins. However, this is sloppy and it means that anyone with Domain Admins or Enterprise Admins can open anyone's mailbox.
I work in a lot of senstive environments (both corporate and government) and management is usually very uncomfortable with the thought that any senior admin can easily open anyone's mailbox. Well, unfortunately, that is just a fact of life with Exchange. Someone with Enterprise Admins or Domain Admins in the root domain can figure out how to do it anyway. However, you can take some steps to make this more difficult.
First, limit access to accounts that are delegated the Exchange Full Admins role to the organization or admin group objects.
Second, the membership in your Domain Admins / Enterprise Admins groups should be less than the number of fingers on your hand (service accounts are the exception, of course). Let me say that again clearly, almost no one should have access to Domain Admins or Enterprise Admins level permissions on a regular basis. And no one should be logging in regularly with these permissions, only as needed.
Anyway, back to why I started this blog entry. Ultimately, you are going to need the ExMerge tool. The latest version of it is found with the Exchange 2003 Tools.
You are also going to need to expose the Security property page for the Exchange oganization object and the admin group objects in Exchange System Manager. It is hidden by default. The registry key is HKCU\Software\Microsoft\Exchange\ExAdmin. In this key, create a REG_DWORD value and set the data value to 1. Then launch Exchange System Manager. Microsoft KB article 259221, XADM: Security Tab Not Available on All Objects in System Manager has more information on this. A little trivia on the Security property page, it was automatically visible in Exchange 2000's betas, but I think too many people got themselves in trouble by removing permissions the thought they did not need.
Now, on to the procedure. In this example, I'll assume that only one user for your entire organization will be used for this, but you can easily do this to individual administrative groups rather than at the organization. Create yourself a user that will ONLY be used for ExMerge operations. I call mine something like ExMergeOperator; this user does not need a mailbox and it should NOT be a member of Domain Admins or Enterprise Admins (they are denied by default, remember?) Protect the password of the ExMergeOperator user so that only an authorized person has it. In some places, they use "two person" integrity, where the security officer has one part of the password and the Exchange admin has the other part.
Next, create a global (or universal) security group called something like Exchange Demi-god Admins. Add the ExMergeOperator in to this group.
Next, using Exchange System Manager, right click on the Organization object and Delegate Control to the Exchange Demi-god Admins group. Delegate the Exchange Full Admins permissions to this group. Then, right click on the organization and display the Security property page, scroll down and locate the group you just created, highlight that group, then scroll down in the permissions until you see the explicit denies for Receive As and Send As.
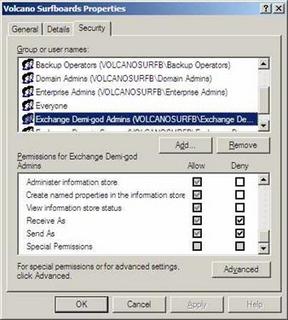 Once you have cleared the Receive As and Send As checkboxes in the Deny column, this user will truly have "complete control" of your Exchange organization.
Once you have cleared the Receive As and Send As checkboxes in the Deny column, this user will truly have "complete control" of your Exchange organization.
Some Exchange gurus are going to look at this and say that the Exchange Demi-god Admins group has too many permissions to the Exchange organization. And this is true. You can scale back the permissions by delegating only the Exchange View Only Admins role, then explicitly assigning only Receive As. The above procedure is just about the simplest, but somewhat secure solution I could quickly write about. More secure solutions are usually somewhat more complex. The important thing is that you protect the use that has these rights.
Finally, from where do you run ExMerge? IMHO, the most efficient place (if you have the local storage for the PST files) is the console of the Exchange server on which you are extracting mail. If this is the case, the Exchange Demi-god Admins group will also need to be delegated permissions to log on locally to the Exchange server console and (probably) access the server through Remote Desktop Connection (you can do this through a GPO).
Granting a user permissions to access mailboxes (even for the sake of performing archives, extracting viruses, or other official work) can be tricky. Make sure management knows that you have this capability and under what circumstances it may have to be used.

1 Comments:
Hello How can i assign the Exmerge rights to just one sigle server in the entire list of server's
Post a Comment
<< Home